Data Centric Security strategies focus on securing the data itself. It is a method to safety that give emphasis to the security of data itself rather than the security of networks, servers, or applications. Data-centric security is progressing speedily as enterprises ever more depend on digital info to run their business and big data projects become mainstream.
 |
| Data Centric Security – Information Driven Security |
Data driven security is a way to deal with data security worldview that underscores the security of the data itself instead of the security of systems, applications, or even essentially information. Long gone are the days when endpoints of the association were restricted to desktops and tablets joined with the LAN and to some degree simple to secure and oversee by local IT managers. Endpoints now included virtual clients, cell phones, tablets, and considerably accomplice associations with a need to trade data. These extra complexities oblige data to be pushed and pulled to gadgets inside and remotely, along these lines expanding the danger of presentation and the probability of information burglary.
In the connected society and arranged economy, a standout among the most important resources is information. The need to confide in your data, systems and calculations utilized as a part of choice making is crucial. The capacity to identify, withstand, react to and recoup from assaults or security breaks is seen as a foundation for business progression. Securing the on-line modern control frameworks and basic base in any vertical industry and in addition securing the complete chain of guardianship in the product inventory network is a key test in an arranged economy. Samples of commercial ventures are logistics, oil and gas, car, mining, assembling and utilities.
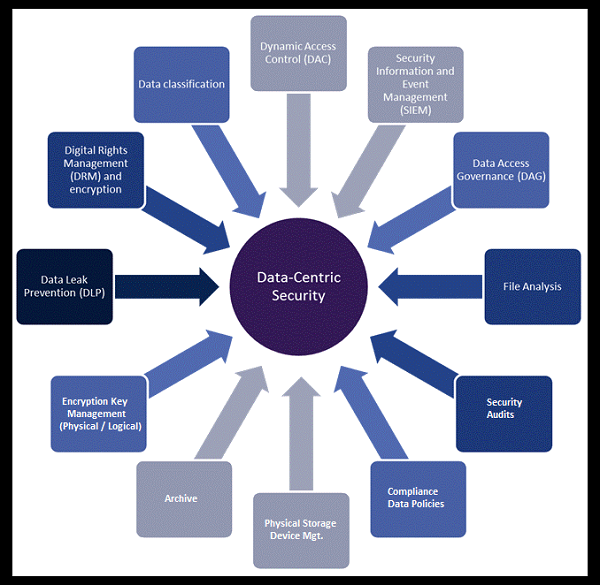
Advices to implement Data-Centric Security
1) Detect the most delicate information: Classify data based on risk, sensitive, compliance necessities.
2) Regulate where your data is at break: Genuine users may have local replicas of your utmost sensitive data. You’ll must able to crawl all likely tracks.
3) Conclude how data is used: Who is retrieving data? Who have to have freedoms? What are users doing through data? Essential questions to answer when observing at data-centric security.
 |
| Data Centric Security |
4) Put on covered security: While securing the data is essential, it’s a keen phase to secure the outer limits with updated firewall, anti-virus , VPN, and data-loss prevention solutions too.
5) Encode data: Disk encryption, data at rest and data in motion are not sufficient; make sure you’re put on file- and application-level encryption with tough authentication and granular control.
6) Always look to improve technology, process with Monitor, review and improve.
3 ethics of a data-centric security structure
·Altering needs to filter content creates security clear to
·Integrating data-access results and allotting application makes security accessible.
·Using metadata instead of files/tables ensures systematic protection of sensitive data.
These will definitely help you to drive authority every single day in information driven security and encryption arrangements. You can also get the best cloud hosting support service providers with an extensive, end-to-end Data-Centric Security, which empowers divergent information sources with different security and consistence necessities to be solidified into a common stage for handling, examination, and application improvement.









